With the increased prevalence of remote work, the simplification of in-house IT management and the prospect of significant cost savings, businesses have accelerated their adoption of cloud services. The benefits are substantial, but companies that rely on such configurations need to be prepared to manage threats from two different directions:
- Business operations and systems could be impacted if the cloud service provider (CSP) undergoes a direct attack, potentially leading to data loss or theft.
- Malicious entities could target the company’s internal network in an effort to attack assets and functionalities housed in the cloud.
Unfortunately, many businesses assume that their CSP is responsible for managing these potential threats. The reality is that providers often contractually relay risks to their customers, meaning your business is ultimately the responsible party in charge of several core cybersecurity tasks. You’ll need to have your own controls and mitigation measures in place in order to manage risk, avert attacks and recover from incidents.
What threats do businesses face in relation to their cloud services?
The two principal cybersecurity risks that companies must seek to mitigate are data loss or exposure and service disruptions.
Data loss or exposure
Cloud accounts can be subject to ransomware attacks, which can result in the temporary or permanent loss of access to critical data. Specifically, this can be accomplished if bad actors are able to compromise connected devices. Accordingly, the risk profile may be higher for companies due to human errors such as unintentionally providing public access, placing sensitive information in wrong storage or public buckets, incorrectly setting bucket and object permissions, having insecure APIs or implementing BYOD (bring your own device) policies that don’t have appropriate safeguards. Other attack vectors may include corporate and personal pathways, as well as rogue devices present on the network. Criminals may also use phishing techniques to steal login credentials for cloud environments.
A successful ransomware attack may be more than just costly and disruptive. It could also result in the organization permanently losing access to important information and records. That’s what happened to an Arizona health care provider recently. According to Health IT Security, Queen Creek Medical Center recently started to inform 35,000 patients that a ransomware attack resulted in the corruption of electronic health records (EHRs).
In addition to inhibited data access or corrupted files, data theft and exposure can also negatively affect targeted companies, resulting in significant reputational damage. T-Mobile reported in August 2021 that the data associated with approximately 40 million prospects and customers was compromised. Headlines like these are becoming all too common, and the impact can last a long time.
Service disruption
If functionalities and services of a CSP are taken offline due to a cyberattack, your business could feel the brunt of that incident. A company that relies on a cloud provider for data storage, infrastructure or vital business applications, including human resources and payroll functions, will experience business continuity difficulties if any of those operations are impeded or even temporarily disrupted.
Insider threats could also interfere with your company’s systems, procedures and applications. Such actions might be undertaken by workers within your organization or those supporting the CSP. This is all the more reason to ensure that you have strong access controls and employment agreements in place to protect your data.
Solutions to help mitigate risks associated with your cloud services
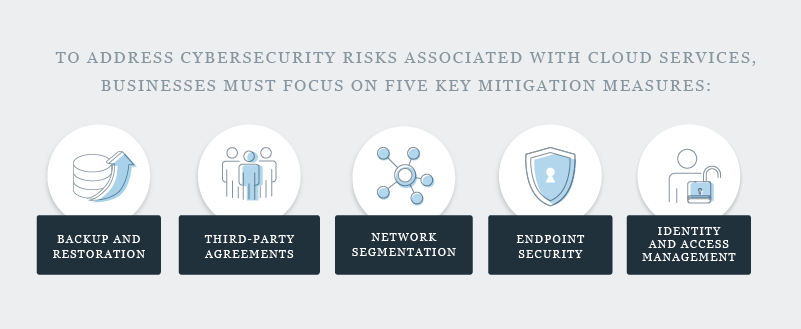
To address cybersecurity risks associated with cloud services, businesses must focus on five key mitigation measures:
- Backup and restoration.
- Third-party agreements.
- Network segmentation.
- Endpoint security.
- Identity and access management.
Backup and restoration
The reality of the cybersecurity landscape today is that, no matter what you do, you’ll likely never reduce your risk of experiencing an incident to zero. As such, you need to have robust contingency plans in place for bouncing back from data loss.
It’s recommended that businesses subscribe to additional backup services, including those with varying redundancy levels beyond the default settings that may be provided by your CSP. This is especially true for companies that have a heightened risk profile, including those that rely on cloud services for a higher proportion of their data and business application needs.
You should also make sure that you have secure configurations and a comprehensive business continuity plan (BCP) in place — perhaps even an adaptive BCP. With such precautions, you’ll know exactly how to respond if you do experience an incident, helping you to minimize potential service disruptions.
Secure contracts and agreements with third parties
When third parties have access to your data, it’s essential that you have strong contracts and agreements in place to verify what protections are being used and to understand how incidents will be handled.
For contracts:
- Make sure that there is language covering data protections and restrictions on employee access.
- Review the company’s incident management procedures and BCP while paying particular attention to guidelines for communicating a breach to users.
In the case of agreements:
- Look for information pertaining to how the third party manages IT security and protects its customers.
- Assess what your responsibilities will be if the third party experiences data loss, a breach or other catastrophic events.
Network segmentation
With effective network segmentation, you may be able to contain the damage if an incident does occur. Make sure to appropriately secure and seclude critical servers and other vital endpoints. An ideal plan includes segmentation of networks based on risk, enhanced security configurations for critical applications and limited vendor access.
Endpoint security
Protect laptops and other endpoints with the appropriate safeguards, such as antivirus and anti-malware software, and provide encryption support when necessary. You should create clear policies for using external drives, too. Endpoint security also entails using network security best practices, such as firewall protection.
Identity and access management (IAM)
IAM protections are crucial, especially for defending your organization from insider threats that may be present within your company as well as coming from the CSP. Make sure that all parties have only the privileges required to conduct their jobs. In addition, it’s vital that you have processes in place to ensure IAM updates are completed immediately following a worker’s departure.
CFGI can help your organization mitigate risks associated with cloud services. Contact our team today for a complimentary 30-minute consultation.

